DevOps vs DevSecOps: How security reshapes software delivery

Last updated on
Friday
November
2025
DevOps vs DevSecOps: How security reshapes software delivery
Remember when "move fast and break things" was the battle cry of software teams everywhere? Those days are gone.
Today's reality: you need to move fast and secure things.
DevOps revolutionized how we build software by breaking down silos between developers and operations teams. But in a world where a single vulnerability can cost millions, speed without security is just faster failure.
Enter DevSecOps: the approach that's changing how leading organizations deliver software by making security everyone's responsibility—not just a final checkpoint.
From Fortune 500 companies to fast-growing startups, teams are discovering that integrating security throughout their delivery pipeline isn't slowing them down—it's preventing the high-profile breaches and outages that really kill momentum.
This article explores the key differences between DevOps and DevSecOps, real-world risks, the DevSecOps maturity model, and best practices that forward-thinking teams are adopting.
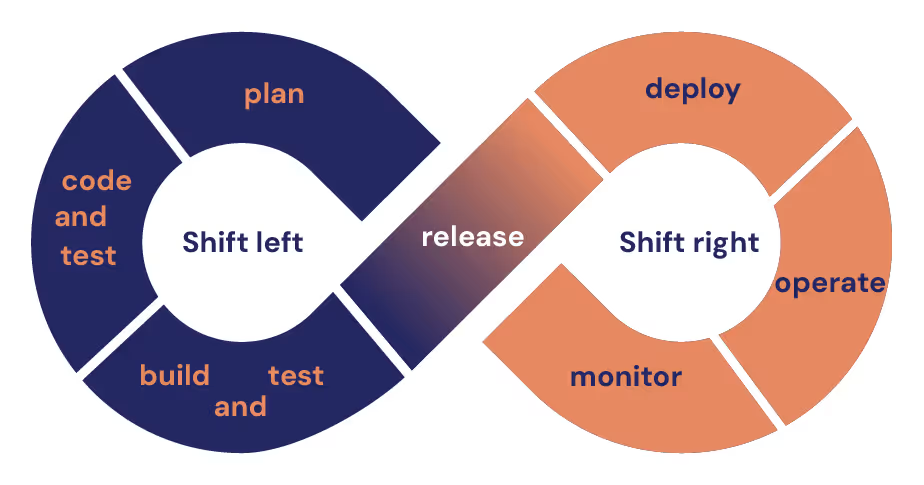
What is DevOps?
DevOps tears down the wall between development and operations teams. Instead of throwing code "over the fence" and hoping for the best, DevOps creates a shared responsibility model with a simple goal: ship better software faster.
The core elements that make DevOps work include:
- Continuous integration and deployment (CI/CD)
- Infrastructure as code (IaC) that removes manual configuration headaches
- Cross-functional collaboration instead of departmental finger-pointing
- Relentless monitoring and automation to catch issues early
The result? Teams deploy more frequently with fewer failures. But there's a catch: security often enters the conversation late, leading to last-minute scrambles, emergency patches, and the dreaded "security said no" moments that kill momentum.sa
What is DevSecOps?
DevSecOps flips the script on the traditional security model. Instead of security being the department of "no" that shows up at the end with a clipboard full of blockers, it embeds security thinking and testing throughout the entire development lifecycle, or what's called "shift left testing."
When DevSecOps is working well, you'll see:
- Security tools running automatically in CI/CD pipelines
- Vulnerability scanning happening with every commit
- Developers trained to write more secure code
- Security, development, and operations teams speaking the same language
According to Datadog's 2025 State of Application Security Report, the most successful DevSecOps teams also apply contextual intelligence; they understand which vulnerabilities matter in their specific environment rather than treating every alert as a five-alarm fire.
How does DevSecOps work?
DevSecOps transforms the traditional software delivery process by integrating security practices at every stage of the development lifecycle rather than tacking them on at the end.
Here's how this works in practice:
1. Planning phase: security by design
In traditional DevOps, planning focuses on features and timelines. In DevSecOps, security requirements and threat modeling become first-class citizens in the planning process.
The security team collaborates with developers from day one, identifying potential vulnerabilities before a single line of code is written.
Threat modeling identifies potential security vulnerabilities early by analyzing the system from an attacker's perspective. By conducting structured threat analyses using frameworks like STRIDE or PASTA, security teams can identify attack vectors, potential threats, and mitigation strategies before development begins, dramatically reducing security issues downstream.
The DevSecOps approach incorporates:
- Threat modeling sessions led by security experts
- Security acceptance criteria for user stories
- Risk assessments for new features
- Selection of appropriate security tools for the project
2. Development: secure coding as standard practice
During development, DevSecOps engineers embrace secure coding practices as part of their daily work:
- Static application security testing (SAST) runs automatically when code is committed
- Dependency scanning checks third-party packages for known vulnerabilities
- Security linting tools flag risky code patterns in real time
- Automated secret detection prevents credentials from being committed
This shift makes security an enabler rather than a blocker in the development process. Engineers receive immediate feedback on security issues, reducing the cost and time of fixing them later.
Modern DevSecOps pipelines integrate these tools directly into developers' workflows. For example, a GitHub Actions workflow might run Snyk for dependency scanning, SonarQube for SAST, and GitGuardian for secret detection with each pull request, providing developers immediate feedback before code ever reaches the main branch.
3. Testing: finding vulnerabilities early
Testing in DevSecOps goes beyond functional testing to include:
- Dynamic application security testing (DAST)
- Interactive application security testing (IAST)
- Fuzz testing to identify unexpected inputs
- Performance testing with Gatling to identify security-related bottlenecks
The DevSecOps workflow integrates these security tests directly into the CI/CD pipeline, automating what was once a manual, time-consuming process handled by separate security teams.
For microservice architectures, this becomes even more critical, as traditional perimeter security is insufficient. Each service needs its own security validation, and the interactions between services require comprehensive testing under various conditions—something Gatling excels at by simulating real-world traffic patterns across distributed systems.
4. Deployment: secure infrastructure and configurations
The DevSecOps approach transforms deployment by:
- Scanning container images for vulnerabilities before deployment
- Validating infrastructure as code (IaC) configurations for security misconfigurations
- Implementing robust access controls and least privilege principles
- Using ephemeral credentials instead of long-lived access keys
Cloud-native environments demand special attention here. Security considerations differ dramatically between development, testing, staging, and production environments.
DevSecOps practices ensure that security controls scale appropriately across environments; development environments might prioritize flexibility, while production environments implement strict guardrails and comprehensive monitoring.
5. Monitoring: continuous security vigilance
In production, DevSecOps practices include:
- Runtime application self-protection (RASP)
- Continuous vulnerability scanning
- Security information and event monitoring (SIEM)
- Automated incident response for known attack patterns
- Performance monitoring to detect anomalous behavior that might indicate security breaches
This continuous security monitoring creates a feedback loop that informs future development, creating a virtuous cycle of continuous improvement in both security and operational efficiency.
Effective security monitoring looks not only for known attack signatures but also for behavioral anomalies. For instance, a sudden spike in database queries might indicate an SQL injection attack, while unusual traffic patterns could signal a DDoS attempt.
Gatling's performance metrics can help establish baseline performance expectations, making anomaly detection more accurate.
Similarities between DevOps and DevSecOps
Both DevOps and DevSecOps share fundamental principles that make them complementary approaches to software delivery.
This table highlights their key similarities:
Key differences between DevOps and DevSecOps
While sharing foundational principles, DevOps and DevSecOps differ in significant ways that impact how software is developed, tested, and deployed:
One notable difference is in risk prioritization: DevSecOps teams apply contextual data—such as whether a vulnerability affects a public-facing app—to reduce noise and focus only on what truly matters.
For instance, Datadog's findings show that less than 20% of critical CVSS vulnerabilities are actually exploitable when context is considered.
Benefits of DevSecOps
Organizations that embrace DevSecOps will definitely get benefits beyond traditional DevOps.
Here are the key benefits that make DevSecOps worth the investment:
1. Earlier detection of security issues
When security testing shifts left in the development lifecycle, vulnerabilities are discovered and fixed when they're cheapest to address. The System Sciences Institute at IBM found that defects cost 6x more to fix in implementation than in design, and 15x more in testing phases.
DevSecOps practices like automated security scanning in CI/CD pipelines catch issues when they're hours old, not months, dramatically reducing remediation costs and time.
2. Reduced security bottlenecks
Traditional security processes often create bottlenecks that delay software delivery. The DevSecOps approach integrates security into development workflows, eliminating last-minute security reviews that typically delay releases.
Research from Gitlab’s Global DevSecOps Report shows that organizations implementing mature DevSecOps practices deploy 3x more frequently than those with siloed security teams.
3. Improved security posture
By making security a continuous concern rather than a periodic checkpoint, DevSecOps significantly strengthens overall security posture. Organizations with mature DevSecOps practices report 50% fewer security vulnerabilities in production compared to those using traditional security approaches.
This is particularly impactful in industries handling sensitive data. Financial services organizations implementing DevSecOps report a 60% reduction in security incidents, while healthcare companies see similar improvements in protecting patient data.
4. Regulatory compliance by design
For regulated industries, DevSecOps transforms compliance from a painful audit exercise to a continuous, automated process. Security considerations and compliance requirements become part of the development process, with automated checks ensuring adherence to standards like GDPR, HIPAA, or PCI-DSS.
5. Enhanced collaboration and shared knowledge
Perhaps the most valuable benefit: DevSecOps breaks down the traditional antagonism between development and security teams. When security experts collaborate closely with developers, knowledge transfer happens naturally. Over time, developers build security expertise, and security teams gain appreciation for development constraints.
This cultural shift creates a continuous improvement cycle where security becomes everyone's responsibility rather than one team's burden.
{{cta}}
Real-world risks driving DevSecOps adoption
1. Java apps are vulnerability magnets
If your stack includes Java, pay attention: as of Q1 2025, a whopping 44% of Java services in production have known-exploitable vulnerabilities. Threats like Log4Shell continue to haunt Java applications long after patches are available. Even worse, Java apps take a median of 62 days to patch critical vulnerabilities—three times longer than JavaScript applications.
The technical challenge stems from Java's deep dependency chains and the extensive use of third-party libraries. For example, a typical Spring Boot application might include over 100 transitive dependencies, each representing a potential attack vector. Reddit users also note that that vulnerable Java applications often exhibit performance degradation under load before security breaches become apparent.
2. Supply chain attacks: the trojan horses of modern software
"It's just a dependency." Until it isn't. In 2024 alone, security teams identified thousands of malicious packages in npm and PyPI repositories. Modern attacks don't kick down your front door; they hide in the packages you willingly install. One compromised dependency can give attackers the keys to your entire kingdom.
These attacks are particularly insidious because they target the trust relationship between developers and package maintainers. For example, an event-stream incident could affect millions of applications when a malicious actor gains control of a widely-used package, injecting cryptocurrency-stealing code that activated only in production environments.
3. Your CI/CD pipeline probably has the digital equivalent of keys under the doormat
More than half of GitHub Actions workflows still use long-lived access credentials instead of temporary, session-based tokens. It's like leaving your house key under the doormat and hoping nobody looks there. These persistent credentials are gold for attackers, offering a path to privilege escalation and lateral movement throughout your systems.
The technical risk emerges when these credentials grant excessive permissions. For instance, a build pipeline may only need read access to a specific repository, but the credentials used might have organization-wide admin rights. If compromised, these credentials allow attackers to move laterally across repositories, manipulating code or injecting malware.
4. Not all vulnerabilities are created equal
Drowning in security alerts? You're not alone. The average service has 13.5 high or critical CVSS vulnerabilities, but here's the kicker: only 18% of them are actually exploitable in your specific environment. DevSecOps teams are moving beyond raw CVSS scores to focus on what really matters: is this vulnerability actually reachable in our production environment?
The technical implementation of contextual vulnerability management requires understanding your application's runtime behavior. For instance, a critical SQL injection vulnerability in an admin interface might be technically severe, but if that interface is only accessible from internal networks and protected by strong authentication, its actual risk is lower than a medium-severity vulnerability in a public-facing API.
5. Your dependencies are probably ancient history
"If it ain't broke, don't update it" is a recipe for a security disaster. The median dependency in production is 215 days behind its latest version. For Java? A staggering 401 days. Applications that deploy infrequently are 47% more outdated than those with regular deployment cycles. Every outdated dependency is a potential security time bomb.
The technical challenge lies in dependency management at scale. Major enterprise applications might use dozens of direct dependencies and hundreds of transitive ones. Each represents a potential vulnerability vector, and updating them requires testing to ensure compatibility. DevSecOps teams are addressing this by implementing automated dependency scanning and scheduled update cycles integrated with comprehensive testing.
6. Bloated containers are security liabilities
When it comes to container images, bigger isn't better, it's dangerous. Container images over 500MB had up to 20 severe vulnerabilities, while minimal images under 100MB had virtually none. Those "helpful" utilities you left in your production containers? They're attack vectors waiting to be exploited.
Technically, the issue stems from unnecessary packages in base images. For example, a container that needs only Python might inherit a full Ubuntu base image with hundreds of utilities. Each component increases the attack surface. Teams are addressing this with multi-stage builds and distroless base images that contain only the runtime necessary for the application.
Performance testing: the critical security component you're missing
Here's an uncomfortable truth: your application can be technically secure but still catastrophically fail when it matters most. When traffic spikes—during Black Friday sales, viral social media moments, or major ticket releases—security vulnerabilities that stay hidden during normal operation suddenly reveal themselves.
When performance issues become security breaches
Under heavy load, your application doesn't just slow down, it changes behavior in ways that can compromise security:
- Resource exhaustion that turns minor traffic surges into complete system outages
- Timeout extensions that accidentally bypass crucial security checks
- Exception handling failures that leak sensitive information in error messages
- Connection pool saturation that enables request hijacking
Standard security scans miss these issues entirely because they test functionality, not resilience under pressure.
For example, in a microservices architecture, services under extreme load may experience timeout cascades. When one service becomes unresponsive, others may implement circuit-breaking patterns that bypass normal authorization flows.
Without proper testing, these "emergency" paths often lack the security controls present in primary flows.
Why your security testing is incomplete without load testing
Leading DevSecOps teams are now integrating performance testing directly into their security validation process. Using tools like Gatling, they simulate extreme traffic conditions to uncover vulnerabilities that only emerge under stress.
Gatling's ability to simulate thousands of concurrent users makes it uniquely positioned to identify these security-under-stress issues. By integrating Gatling into the CI/CD pipeline, teams can automatically verify that security controls remain functional even at 10x or 100x normal load—something traditional security scanning simply cannot validate.
DevSecOps best practices that actually work
Want to upgrade your DevSecOps game? These best practices focus on integrating security considerations throughout the development lifecycle, creating a robust foundation for your DevSecOps transformation.
Focus on these high-impact security practices:
- Make infrastructure code, not prayer: Use tools like Terraform or CloudFormation to eliminate configuration drift and ensure consistent security measures.
- Kill long-lived credentials: Replace permanent access keys with short-lived, OIDC-based tokens that expire automatically.
- Prioritize vulnerabilities that matter: Stop treating every CVSS 9+ score as a five-alarm fire. Use runtime context to focus on what's actually exploitable.
- Update dependencies religiously: Your update cadence is your security pulse. Stale dependencies = security debt.
- Shrink your containers: The smaller your container images, the fewer vulnerabilities you'll have. Challenge every utility and package.
- Automate, automate, automate: If a security check can be automated, it should be. Human-only security processes don't scale.
- Test performance under pressure: Use tools like Gatling to stress test your applications and find security vulnerabilities that only appear under load.
- Normalize blameless reviews: When security issues happen (and they will), focus on fixing the process, not finding a scapegoat.
- Implement secure coding practices: Train developers on security best practices and provide them with code templates and libraries that enforce security by default.
- Establish security policies early: Create clear security requirements that are included in the definition of "done" for every feature.
DevSecOps maturity: A roadmap for technical leaders
Transforming your organization's approach to security isn't a one-day project. Before jumping in, answer these three critical questions:
- Where are we today? (Brutal honesty required.)
- Where do we need to be? (Based on your risk profile, not a checklist.)
- How do we close the gap? (Incremental wins > perfect plans.)
The DevSecOps Maturity Model gives you a framework to answer these questions across six competency areas: people and culture, plan and develop, build and test, release and deploy, operate, observe and respond.
The most mature organizations don't just shift security left, they distribute it throughout the entire pipeline, from initial design to production monitoring. DevSecOps engineers work alongside traditional DevOps engineers to ensure security is never an afterthought in the software delivery process.
Leaders should use a self-assessment to identify gaps and prioritize initiatives by competency. This approach allows for targeted investments in the areas that will yield the greatest security improvements.
Which one to choose: DevOps or DevSecOps?
The question of DevOps vs DevSecOps is more about evolution than features.
Here's how to think about this decision for your organization:
For organizations new to modern software delivery
If you're just beginning your journey away from traditional development processes, starting with core DevOps practices provides a solid foundation:
- Focus first on automating your CI/CD pipeline and establishing infrastructure as code
- Build collaboration between development and operations teams
- Implement monitoring and establish feedback loops
- Create a continuous delivery culture
Once these fundamentals are in place, you can begin integrating security practices incrementally. This phased approach prevents teams from being overwhelmed by too much change at once.
For established DevOps organizations
If you already have mature DevOps practices, evolving toward DevSecOps should be your clear next step:
- Identify your most significant security risks and address those first
- Integrate automated security testing into your existing CI/CD pipeline
- Build relationships between development and security teams
- Update your definition of "done" to include security requirements
- Invest in upskilling developers on secure coding practices
For high-risk or regulated industries
For organizations in financial services, healthcare, government, or other regulated sectors, DevSecOps isn't optional:
- Start with a comprehensive security and compliance assessment
- Implement security gates in your deployment process
- Establish automated compliance checking for your specific regulatory requirements
- Consider using specialized DevSecOps tools designed for your industry
- Invest in robust security testing, including performance testing under load with Gatling
Each industry faces unique challenges:
- Financial services: Need to balance security with ultra-low latency requirements while maintaining compliance with regulations like PSD2 and SOX
- Healthcare: Must protect sensitive patient data (PHI) in compliance with HIPAA while ensuring system availability for critical care
- Retail/E-commerce: Need to secure customer payment data while handling extreme traffic spikes during sales events
- Software vendors: Must secure their software supply chain to prevent downstream impacts to customers
The verdict: evolution, not revolution
For most organizations, the choice isn't binary. The most successful approach involves starting with DevOps fundamentals and evolving toward DevSecOps as your team matures. This progression allows cultural changes to take root while technical practices evolve.
Remember: DevSecOps is the natural evolution of the DevOps practice to address the security challenges of modern software delivery.
The future belongs to the secure and scalable
DevSecOps isn't a passing trend. As digital experiences become more critical to business success, the old "speed vs. security" tradeoff no longer matters.
The leaders of tomorrow aren't choosing between moving fast and being secure. They're building systems that do both by design.
This transformation requires more than a new tool stack. It requires you to change how teams collaborate, how risks are evaluated, and how performance and security testing work together to create truly resilient systems.
The most successful organizations have discovered that security without performance testing is incomplete, and performance without security is dangerous. By bringing these disciplines together with tools like Gatling Enterprise Edition, they're delivering experiences that stay secure and stable, even when traffic explodes, trends go viral, and customer expectations soar.
Want to see how Gatling Enterprise helps leading organizations identify security vulnerabilities under load before they become headlines? Request a demo today and discover the missing piece in your DevSecOps puzzle.
{{cta}}
FAQ
FAQ
DevOps focuses on collaboration between development and operations to deliver software faster. DevSecOps extends this by embedding security practices into every stage of the pipeline.
With rising threats like supply chain attacks and vulnerabilities in open-source code, DevSecOps ensures that security is not an afterthought but a shared responsibility across teams.
No—if done right, DevSecOps accelerates delivery by automating security checks in CI/CD. This reduces late-stage fixes and makes releases safer without adding bottlenecks.
Start by shifting security left: integrate automated scans, train teams in secure coding, and use infrastructure as code. Gradually build a culture where developers, ops, and security collaborate from the start.
Related articles
Ready to move beyond local tests?
Start building a performance strategy that scales with your business.
Need technical references and tutorials?
Minimal features, for local use only




