What is DevSecOps? A guide to secure software development

Last updated on
Friday
November
2025
What is DevSecOps? A guide to secure software development
As a DevOps engineer, you're always under fire. Development teams want rapid feature deployment. Security teams want comprehensive testing and reviews. Business stakeholders want both speed and bulletproof reliability. You're the one who has to make it all work without compromising on any front.
Your application is technically "secure" according to every tool in your pipeline, yet here you are watching a security incident unfold in real time. The root cause? A database query that works fine under normal load but becomes a liability when thousands of users hit your system simultaneously.
Stuff like this happens on the daily, showing how most organizations approach DevSecOps. While everyone focuses on scanning code for vulnerabilities and checking compliance boxes, they're missing a fundamental truth: performance and security are inseparable.
That incident could have been prevented with a comprehensive DevSecOps approach that treats performance as a first-class security concern. Let's explore how DevSecOps can transform your workflow and why performance testing belongs in every security pipeline.
Understanding DevSecOps: Core definition and the performance gap
DevSecOps stands for development, security, and operations, representing a fundamental evolution of the traditional DevOps practice. It integrates security testing and considerations at every stage of the software development process, transforming security from a separate, final checkpoint into a continuous, collaborative responsibility shared across development teams, the security team, and operations team.
The practice emphasizes a "shift-left" mindset, embedding security early and continuously throughout the development process rather than treating it as a post-development checkpoint. Traditionally, DevSecOps focuses on code vulnerabilities, dependency scanning, and compliance checks. These security practices are critical, but there's a significant gap: performance is often left out of the conversation. And that's a problem.
DevSecOps represents a significant departure from conventional software development methods, where security testing was traditionally a separate process that occurred after software was built. This old approach created bottlenecks and delays that couldn't keep pace with modern development timelines and rapid software delivery cycles.
DevSecOps addresses these limitations by detecting vulnerabilities throughout the software development and delivery process, improving the entire software development lifecycle (SDLC).
{{cta}}
Understanding DevSecOps: Core definition and the performance gap
The DevSecOps market is experiencing extraordinary growth, and this has real implications for your day-to-day work as a DevOps engineer.
The global DevSecOps market was valued at $5.1 billion in 2024 and is projected to reach $86.4 billion by 2037, growing at a 23.4% compound annual growth rate. This growth is driven by rising cyber threats and accelerated cloud adoption, two factors that directly impact your work environment and the systems you're responsible for maintaining.
Here's what this means for you:
- Tool ecosystem expansion: More vendors are investing heavily in DevSecOps solutions, which means better tools, more integration options, and competitive pricing. You'll have access to more sophisticated automation capabilities and better open source alternatives.
- Skills in high demand: Organizations are actively seeking DevOps professionals who understand security integration. This growth translates to better job prospects, higher salaries, and more opportunities to specialize in security automation.
- Organizational buy-in: The market momentum makes it easier to get executive support for DevSecOps initiatives. When you propose security automation projects, you're more likely to get the budget and resources you need.
- Industry standardization: As the market matures, best practices are becoming more established. This means clearer implementation patterns, better documentation, and proven approaches you can follow rather than pioneering everything from scratch.
- Pressure to adopt: The flip side is that organizations are under increasing pressure to implement DevSecOps practices. If your company isn't already on this path, you'll likely be tasked with leading the transformation soon.
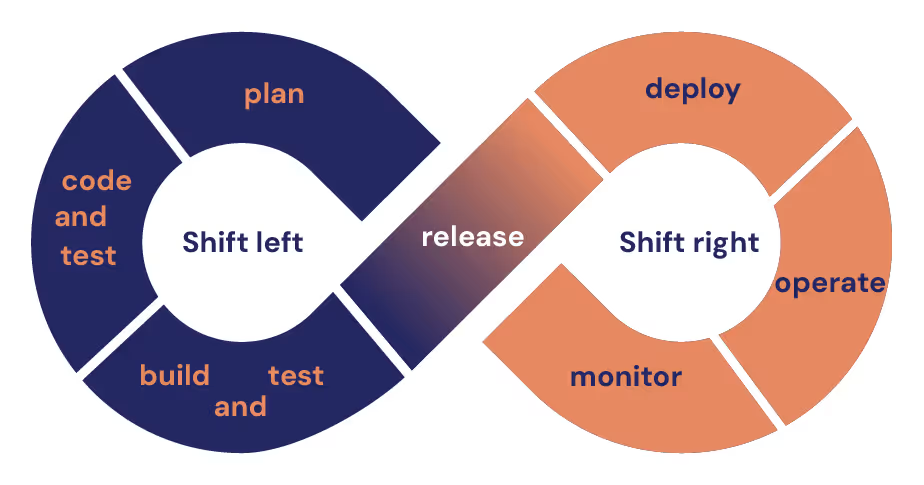
Benefits of DevSecOps: Beyond traditional security
DevSecOps delivers transformative improvements that directly impact your daily workflow and long-term career prospects. Here's what actually happens when you implement DevSecOps properly.
Faster issue resolution
Organizations with mature DevSecOps programs resolve vulnerabilities 11.5 times faster than those without comprehensive security practices. This means fewer emergency patches, less firefighting, and more time for strategic work instead of reactive fixes.
Reduced production incidents
Teams implementing DevSecOps report 50% fewer vulnerable applications compared to traditional approaches. For you, this translates to fewer weekend calls, more stable deployments, and significantly less stress from security-related outages.
Early cost savings
Reduce costs through early mitigation of security issues before they reach production. Catching problems in development rather than production means smaller fixes, less downtime, and avoiding the exponential costs of post-deployment security patches.
Automated security integration
Automated security checks, performance testing, and compliance verification eliminate manual security reviews that traditionally slow down deployments. You can maintain rapid release cycles without sacrificing security standards.
Enhanced performance resilience
Performance testing reduces downtime risk and prevents denial-of-service-like failures. This means your applications remain stable under load, protecting both user experience and system security simultaneously.
Reliable scaling capabilities
DevOps Enables reliable scaling critical for business continuity in high-stakes digital environments. Your infrastructure can handle traffic spikes without compromising security posture or exposing sensitive data.
Shared responsibility model
By making security a shared responsibility among development teams, security professionals, and operations, the burden no longer falls solely on operations teams to "fix security later." Everyone contributes to security throughout the development process.
DevSecOps is built upon several foundational principles that distinguish it from traditional security approaches:
Core principles and methodology
DevSecOps isn't just a set of tools you bolt onto your existing pipeline. Think of it as rewiring your entire approach rather than adding another layer of complexity.
DevSecOps is built upon several foundational principles that distinguish it from traditional security approaches:
Shift-left security (including performance)
Remember the last time you discovered a security flaw three days before a major release? That sinking feeling when you realized the "quick fix" would require rebuilding half your authentication system? Shift-left security prevents exactly this scenario.
The most critical DevSecOps principle involves integrating both security and performance considerations early in the development process. Instead of treating security as a gate at the end, you're building it into every commit, every code review, every deployment decision.
Automation
Manual security reviews are where good intentions go to die. You know the drill: developers waiting three weeks for security sign-off, security teams drowning in tickets, and everyone frustrated with the bottleneck.
Automated security checks, performance testing, code analysis, and compliance verification eliminate this friction entirely. Your CI/CD pipeline becomes intelligent enough to catch issues without human intervention. The result? You maintain rapid release cycles while actually improving security standards. No more "security versus speed" trade-offs.
Collaboration
Here's where most organizations fail spectacularly. They mandate "DevSecOps" but keep the same organizational silos that created the problem in the first place.
Breaking down traditional barriers between security teams, developers, and operations isn't about having more meetings. It's about shared tools, shared metrics, and shared accountability. When a vulnerability surfaces, everyone understands their role in the fix. Security teams learn how deployment pipelines work. Developers understand threat models. Operations teams see security as operational resilience, not external compliance theater.
This collaborative DevSecOps culture creates something powerful: collective ownership of security outcomes.
Continuous monitoring
Production is where your theories meet reality. All the scanning and testing in the world means nothing if you can't see what's actually happening when real users hit your systems.
Ongoing monitoring and testing in production environments serve as your early warning system. Performance degradation that could signal an attack. Unusual error patterns that might indicate exploitation attempts. Authentication failures that suggest credential stuffing. The key is connecting these signals to actionable responses rather than just generating more dashboard noise.
Risk assessment
Every development decision carries security implications. The database optimization that improves performance but changes error handling behavior. The caching layer that speeds up responses but might leak data between users. The API endpoint that makes mobile integration easier but expands your attack surface.
Continuous risk assessment means these trade-offs become explicit conversations rather than hidden assumptions. Security and performance considerations inform all development decisions through ongoing evaluation rather than post-hoc security reviews that inevitably miss context.
{{card}}
Key components of a DevSecOps toolchain
A robust DevSecOps implementation requires a comprehensive toolchain spanning the entire delivery lifecycle:
Core Infrastructure
- Source control and collaboration: Git, GitHub, GitLab
- CI/CD pipelines: Jenkins, GitHub Actions, GitLab CI/CD, Azure DevOps
- Infrastructure-as-Code & Configuration: Terraform, Ansible
Security sanning tools
- Static Application Security Testing (SAST): SAST tools analyze source code for known vulnerabilities
- Dynamic Application Security Testing (DAST): Tests running applications for security flaws
- Software composition analysis: Identifies vulnerabilities in open source components
- Dependency scanning: Snyk, OWASP Dependency Check for detecting known vulnerabilities
Monitoring and observability
- Monitoring tools: Prometheus, Grafana, ELK Stack, Splunk
Performance testing
- Gatling: Bridges QA, Operations, and Security by automating performance testing as part of your secure delivery pipeline. Gatling serves as a critical DevSecOps tool that bridges quality assurance, operations, and security teams, ensuring that applications not only pass security tests but can also maintain security posture under real-world load conditions.
Best practices for embedding performance in DevSecOps
Now that you understand why performance belongs in your security pipeline, let's get practical. These aren't theoretical frameworks - they're battle-tested approaches you can implement starting next week.
The key is treating performance and security as inseparable concerns rather than parallel workstreams that occasionally intersect.
Shift right: Production-first performance security
While everyone talks about shifting left, the real insights come from shifting right into production environments. Your staging environment will never replicate the complexity of real user behavior, network conditions, and data volumes that expose performance-based security vulnerabilities.
Actionable steps:
- Deploy synthetic user journeys that constantly test critical security paths in production
- Implement canary deployments with performance gates that automatically roll back if response times degrade
- Use feature flags to test performance under different user loads while maintaining security controls
Pro tip: Set up load testing scenarios that deliberately stress your system while monitoring for security implications. A 10-second response time might be annoying in staging, but in production it could mean exposed session tokens or failed authentication attempts.
Automate performance testing with security context
Most performance testing treats security as an afterthought. Flip this approach by making security scenarios the foundation of your performance tests.
Actionable steps:
- Create user personas for your Gatling tests that include different privilege levels (anonymous, authenticated, admin)
- Test authentication flows under load to ensure login systems don't leak information during high traffic
- Simulate attack patterns like credential stuffing or API abuse to verify your rate limiting holds up
Pro tip: Run your performance tests against production-like data volumes, not the sanitized datasets from staging. Real customer data patterns reveal edge cases that clean test data never will.
Define performance SLAs that include security metrics
Traditional SLAs focus on uptime and response times. DevSecOps SLAs need to include security posture under load.
Actionable steps:
- Set error rate thresholds that account for security-related failures (failed authentications, blocked requests)
- Define "security-weighted" response times where authentication and authorization steps have stricter requirements
- Include time-to-detect metrics for security incidents that originate from performance issues
Pro tip: Create SLA dashboards that show security and performance metrics side by side. When response times spike, you should immediately see if authentication failure rates are also climbing. Your monitoring strategy should treat performance anomalies as potential security indicators, not just operational problems.
Actionable steps:
- Correlate performance metrics with security events using performance testing tools
- Set up intelligent alerting that escalates differently for performance issues during off-hours (potential indicator of attack)
- Implement automated response playbooks that trigger security scans when performance degrades unexpectedly
Pro tip: Train your monitoring system to recognize the performance signatures of common attacks. DDoS attempts, credential stuffing, and API abuse all have distinctive performance fingerprints you can detect early.
Security controls that scale with performance
The biggest DevSecOps failure is implementing security controls that break under load. Design your security architecture to be performance-aware from day one.
Actionable steps:
- Load test your WAF and rate limiting to ensure they don't become bottlenecks
- Implement circuit breakers for security services like authentication providers
- Use caching strategically for security decisions while maintaining audit trails
Pro tip: Document the performance cost of each security control. Know exactly how much latency your authentication adds, how your encryption affects throughput, and where your security scanning creates bottlenecks. You can't optimize what you don't measure.
Actionable quick wins
Start here if you're just beginning to integrate performance into your DevSecOps pipeline:
- Week 1: Add a simple Gatling test that hits your login endpoint under moderate load
- Week 2: Set up monitoring that correlates 5xx errors with authentication failures
- Week 3: Create a performance regression gate for your most critical API endpoints
- Week 4: Implement canary deployments with performance rollback triggers
Pro Tip: Don't try to boil the ocean. Pick one critical user journey, instrument it thoroughly for both performance and security, and use that as your template for expanding to other parts of your system.
Implementation challenges
Despite clear benefits, organizations face several challenges when adopting DevSecOps:
Cultural and organizational barriers
71% of CISOs still view security as a bottleneck to rapid deployment, highlighting persistent cultural barriers. Only 22% of organizations had a formal DevSecOps strategy in 2022, though 62% were evaluating adoption. However, in 2024, SDLC pipeline security has become the top priority for companies according to Gitlab.
Building a DevSecOps culture requires changing how developers, security professionals, and operations teams collaborate throughout the development process.
Security assurance gaps
Over 50% of organizations lack comprehensive security testing, often relying on fragmented tools rather than integrated security approaches. This includes insufficient cloud security measures and incomplete vulnerability management processes.
Technical integration challenges
60% of DevSecOps teams cite technical tooling challenges as adoption blockers, reflecting the complexity of integrating diverse security tools into existing development workflows.
Data management
Managing the vast amounts of observability and security data generated by DevSecOps practices strains teams, necessitating better tooling for actionable insights and effective security operations.
Regional and sectoral adoption
North America dominated the DevSecOps market in 2023 with a 42% share, while the Asia-Pacific region is expected to experience the highest growth rate. Large enterprises lead adoption efforts, with IT, healthcare, and retail emerging as key sectors. France is also among the leaders of DevSecOps adoption according to Gitlab’s survey. Cloud-based solutions account for 70% of deployments, reflecting the shift toward cloud-native development practices and enhanced cloud security requirements.
The path forward
The convergence of development, security, and operations creates unprecedented opportunities for DevOps engineers who understand the full stack. 68% of organizations are adopting AI/ML tools for cloud security, enhancing threat detection capabilities and enabling automated response to security incidents.
We're at an inflection point. The next five years will separate organizations that treat security as a compliance checkbox from those that make it a competitive advantage. As a DevOps professional, you're positioned at the center of this transformation.
You're not just keeping the lights on anymore; you're architecting the security posture of entire organizations.
The skills you're building today in DevSecOps will define your career trajectory. Security automation, performance resilience, and integrated toolchains are becoming the baseline expectations for senior technical roles. Get ahead of this curve, and you'll find yourself with leverage in salary negotiations, choice in job opportunities, and influence in strategic technical decisions.
Security that just works
Imagine a world where security doesn't slow you down but actually accelerates your delivery. Where performance testing automatically prevents the security incidents that currently wake you up at night. Where your CI/CD pipeline is so intelligent that it catches vulnerabilities, performance regressions, and compliance issues before they become your problem.
This isn't science fiction. Organizations are already building these capabilities, and the market momentum shows this approach is becoming the standard, not the exception.
Building tomorrow's infrastructure
By 2037, software supply chains are expected to widely embed strict verification protocols to mitigate credential-based attacks, reflecting the growing adoption of zero-trust security principles. Every security control you automate, every performance test you integrate, every monitoring dashboard you build is infrastructure that will serve your organization for years to come. You're not just solving today's problems; you're preventing tomorrow's.
The organizations that invest in comprehensive DevSecOps now will have unassailable competitive advantages: faster time to market, higher system reliability, and customer trust that can't be bought with marketing budgets.
The ripple effect
Your work implementing DevSecOps doesn't just improve your current project or organization. You're contributing to an industry-wide transformation that raises the security baseline for everyone. Every vulnerability caught in CI instead of production. Every performance regression prevented before customer impact. Every security incident avoided through proactive monitoring.
The integration of open source tools continues to grow, with organizations implementing comprehensive strategies to manage open source components and their associated vulnerabilities.
The overlooked link: Performance as a security concern
The market has spoken. The tools are maturing. The practices are proven. The only question is whether you'll be leading this transformation or following it.
The future belongs to teams that can build software that's fast, secure, and resilient by default. DevSecOps with integrated performance testing is how you get there.
Here's a reality that many organizations miss: Poor performance is a security vulnerability.
How performance issues create security risks
- Timeouts and inconsistent behavior: Slow responses and timeouts can cause applications to behave inconsistently, potentially exposing logic flaws that attackers can exploit.
- Load-based vulnerabilities: Under heavy load, unoptimized endpoints may crash, hang, or leak sensitive state information through error messages or incomplete transactions.
- System degradation: Performance bottlenecks can cause cascading failures that expose internal system details, database schemas, or API endpoints that should remain hidden.
How Threat Actors Exploit Performance Issues
Sophisticated attackers actively exploit performance weaknesses:
- Fuzzing rate limits to find endpoints that behave differently under stress
- Overwhelming APIs with requests to trigger error conditions that leak information
- Creating denial-of-service conditions that force applications into vulnerable states
- Triggering cascading failures that expose internal system architecture
Getting started with Gatling for DevSecOps
Ready to close the performance gap in your security pipeline? Here's your step-by-step implementation guide. We'll focus on the essentials that deliver immediate value without overwhelming your existing workflow.
Think of this as your first sprint toward integrated performance security testing.
Prerequisites
- Gatling OSS or Enterprise
- Existing CI/CD pipeline (GitHub Actions, Jenkins, GitLab, etc.)
- Basic understanding of your application's critical user journeys
Implementation steps
- Define critical test scenarios
- User login and authentication flows
- Payment processing or checkout procedures
- API calls handling sensitive data
- Create automated Gatling simulations
- Develop realistic load patterns based on actual usage
- Include edge cases and stress scenarios
- Test both normal and peak load conditions
- Set performance thresholds
- Define pass/fail criteria for response times
- Establish acceptable error rates
- Set throughput requirements
- Integrate with CI/CD pipeline
- Hook Gatling tests into your existing DevOps process
- Configure automatic execution on code commits
- Set up deployment gates based on performance results
- Monitor and report results
- Surface performance results on team dashboards
- Integrate with existing observability tools
- Provide immediate feedback to development teams
Make performance a part of your pipeline
DevSecOps is about building secure, resilient, scalable software, but security without performance is incomplete. Performance is a key part of the security mission, yet it's often ignored in traditional DevSecOps implementations.
By embedding performance testing tools like Gatling into DevSecOps pipelines, teams can close a critical gap in their security posture. This integrated DevSecOps process helps deliver software that's not just secure on paper, but truly ready for real-world conditions and resistant to performance-based attacks.
Remember: Secure isn't secure if it doesn't scale. The future belongs to organizations that can seamlessly blend speed, security, and performance. DevSecOps with integrated performance testing provides the framework to achieve this critical balance.
Don't leave performance to chance. Start integrating Gatling into your DevSecOps pipeline today and close the security gap that many organizations overlook.
FAQ
FAQ
DevSecOps is the practice of integrating security into every stage of the software development lifecycle, making it a shared responsibility across teams.
DevOps focuses on speed and collaboration between development and operations, while DevSecOps adds security as a core part of the process
It helps prevent vulnerabilities, reduces risks of breaches, and ensures secure software delivery without slowing down development.
Begin by shifting security left—use automated scans, secure coding practices, and collaborate across dev, ops, and security teams.
Related articles
Ready to move beyond local tests?
Start building a performance strategy that scales with your business.
Need technical references and tutorials?
Minimal features, for local use only




